Some REST clients as well as Salesforce applications require servers to present the server certificate along with the chain of certificates up the trust chain all the way upto root certificate. If only the server certificate is presented, then the client may throw an exception like
In order to overcome the above exception, you have configure your web server to present the complete chain. In cases where SSL connection is terminated at the Amazon Load Balancer, you will have to configure the chain in the below configuration of the ELB's "Listener" page:
-----BEGIN CERTIFICATE-----
...
-----END CERTIFICATE-----
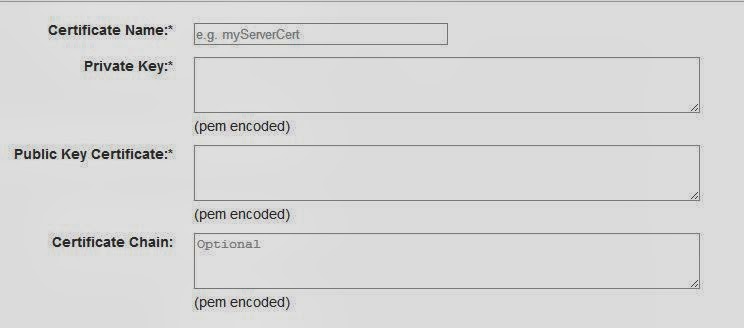
4. Paste intermediate and root certificate in the "Certificate Chain" box:
-----BEGIN CERTIFICATE-----
...
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
...
-----END CERTIFICATE-----
Once the above has been configured, you can choose this for the https port on the ELB.
System.VisualforceException: javax.net.ssl.SSLHandshakeException: sun.security.validator.ValidatorException: PKIX path building failed: sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to requested target
In order to overcome the above exception, you have configure your web server to present the complete chain. In cases where SSL connection is terminated at the Amazon Load Balancer, you will have to configure the chain in the below configuration of the ELB's "Listener" page:
- Give the certificate a name in the "Certificate Name" box.
- Paste unencrypted RSA private key in pem format in the "Private Key" box:
-----BEGIN RSA PRIVATE KEY-----
...
-----END RSA PRIVATE KEY-----
3. Paste X509 public certificate in pem format in the "Public Key Certificate" box:
...
-----END CERTIFICATE-----
4. Paste intermediate and root certificate in the "Certificate Chain" box:
-----BEGIN CERTIFICATE-----
...
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
...
-----END CERTIFICATE-----
Once the above has been configured, you can choose this for the https port on the ELB.
No comments:
Post a Comment